Infosec experts have spotted a nasty variant of a banking malware – dubbed Dyre Wolf – which involves a sophisticated two-factor authentication workaround that has apparently led to the theft of more than $1m from the biz world.
Wrongdoers have demonstrated what IBM Security described as "a brazen twist from the once-simple Dyre malware", which The Register has previously reported on.
The attack – which targets orgs that regularly carry out wire transfers with large sums of money – has proved to be a cash-generating campaign for the baddies courtesy of "sophisticated social engineering tactics", Big Blue said.
Worse still, IBM securo bods John Kuhn and Lance Mueller warned that, in many instances, antivirus tools had failed to detect the malware.
IBM reckoned that, according to its "cyber security intelligence index", a whooping 95 per cent of all attacks relied on a form of human error to successfully pinch cash from unsuspecting folk.
The researchers added:
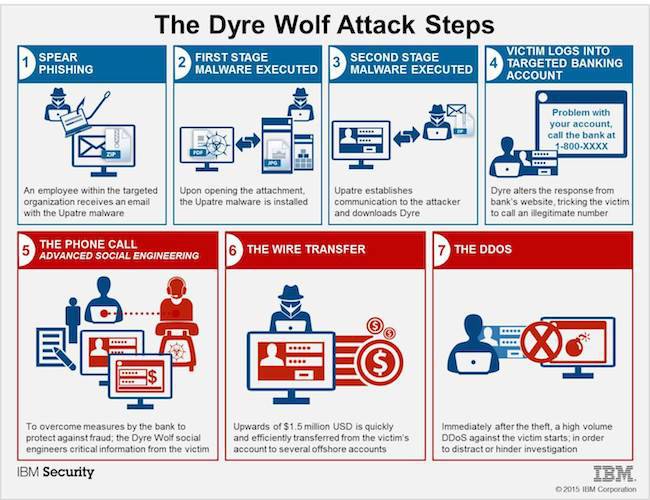
Once the infected victim tries to log in to one of the hundreds of bank websites for which Dyre is programmed to monitor, a new screen will appear instead of the corporate banking site. The page will explain the site is experiencing issues and that the victim should call the number provided to get help logging in.
One of the many interesting things with this campaign is that the attackers are bold enough to use the same phone number for each website and know when victims will call and which bank to answer as. This all results in successfully duping their victims into providing their organizations’ banking credentials.
As soon as the victim hangs up the phone, the wire transfer is complete. The money starts its journey and bounces from foreign bank to foreign bank to circumvent detection by the bank and law enforcement. One organization targeted with the campaign also experienced a DDoS. IBM assumes this was to distract it from finding the wire transfer until it was too late.
Dark in the city night is a wire ... hungry like the wolf. Image credit: IBM Security
Big Blue's full fat version of the Dyre Wolf campaign can be viewed here (PDF). ®
Sponsored: Designing and building an open ITOA architecture
from ffffff http://go.theregister.com/feed/www.theregister.co.uk/2015/04/04/dyre_wolf_malware_ibm_security/
via IFTTT







0 comentarios:
Publicar un comentario